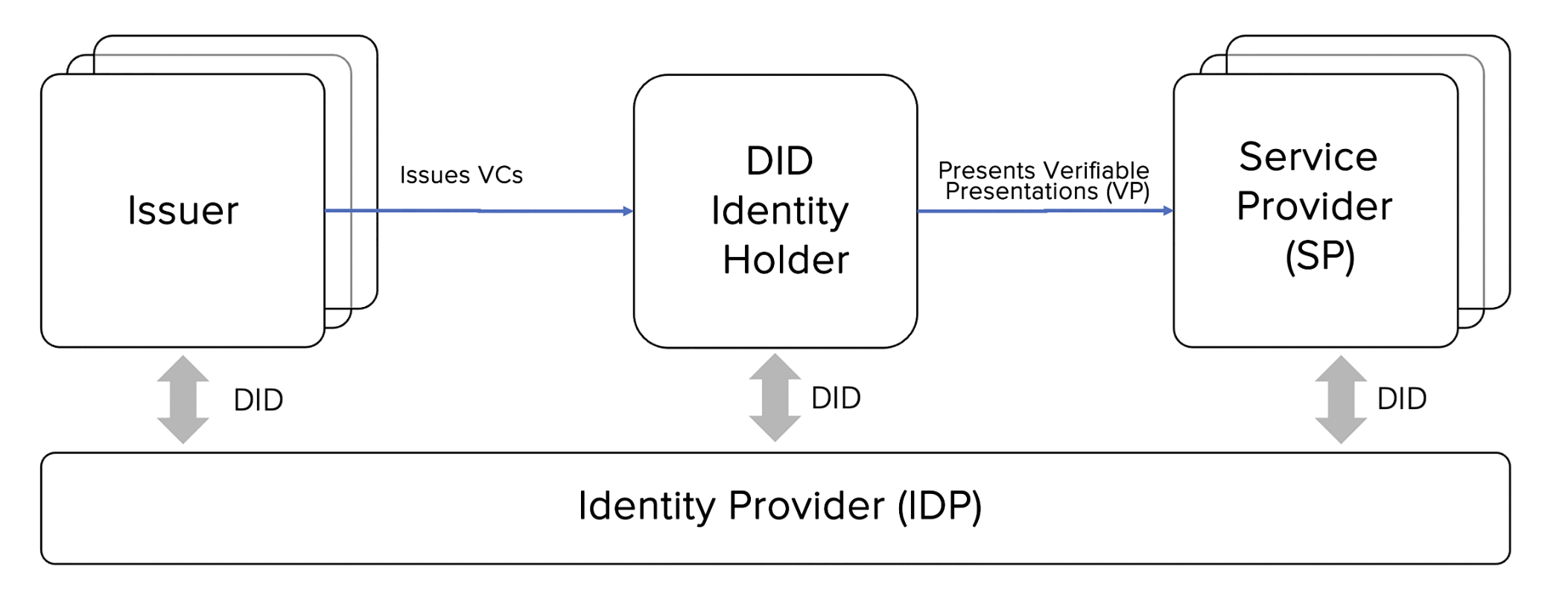
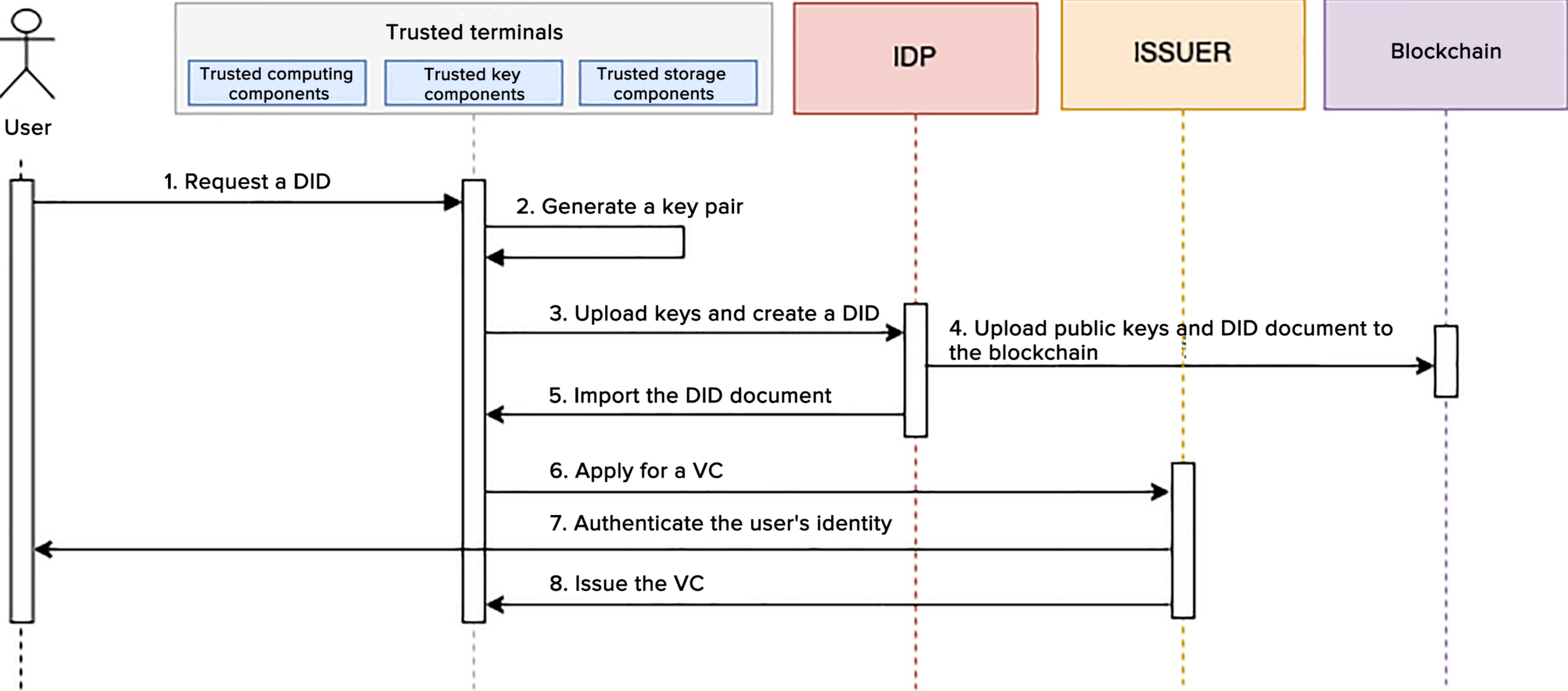
The IIFAA decentralized trusted authentication system's technical architecture is depicted in Figure 2. This
architecture includes underlying storage, a unified service and control platform, the IIFAA ecosystem operation
platform, issuers, the decentralized trusted authentication infrastructure, service providers, and user sides.
The underlying storage module is primarily responsible for the public display of DID identity documents on the
blockchain, using smart contract capabilities for adding and modifying DID documents. The unified service and control
platform manages organizational entities, trust anchoring, and is responsible for VC presentation traceability and
statistics. It ensures the trusted entry of VC issuing organizations and the trusted access of identity service
providers and conducts VC presentation tracing and auditing for unified management and standardized growth. The IIFAA
ecologic operation platform handles VC template management, service scenario management, and service administration. It
is responsible for the configuration, application, and approval processes of various VC templates and service scenarios,
as well as user service management. Issuers and service providers primarily focus on VC issuance and validation. The
decentralized trusted authentication infrastructure offers general SaaS capabilities, such as interactions between
identity services and blockchain, user private key escrow, and VC presentation escrow and traceability. The user side is
responsible for managing user VCs and presentations, as well as handling decentralized identities on user terminals.
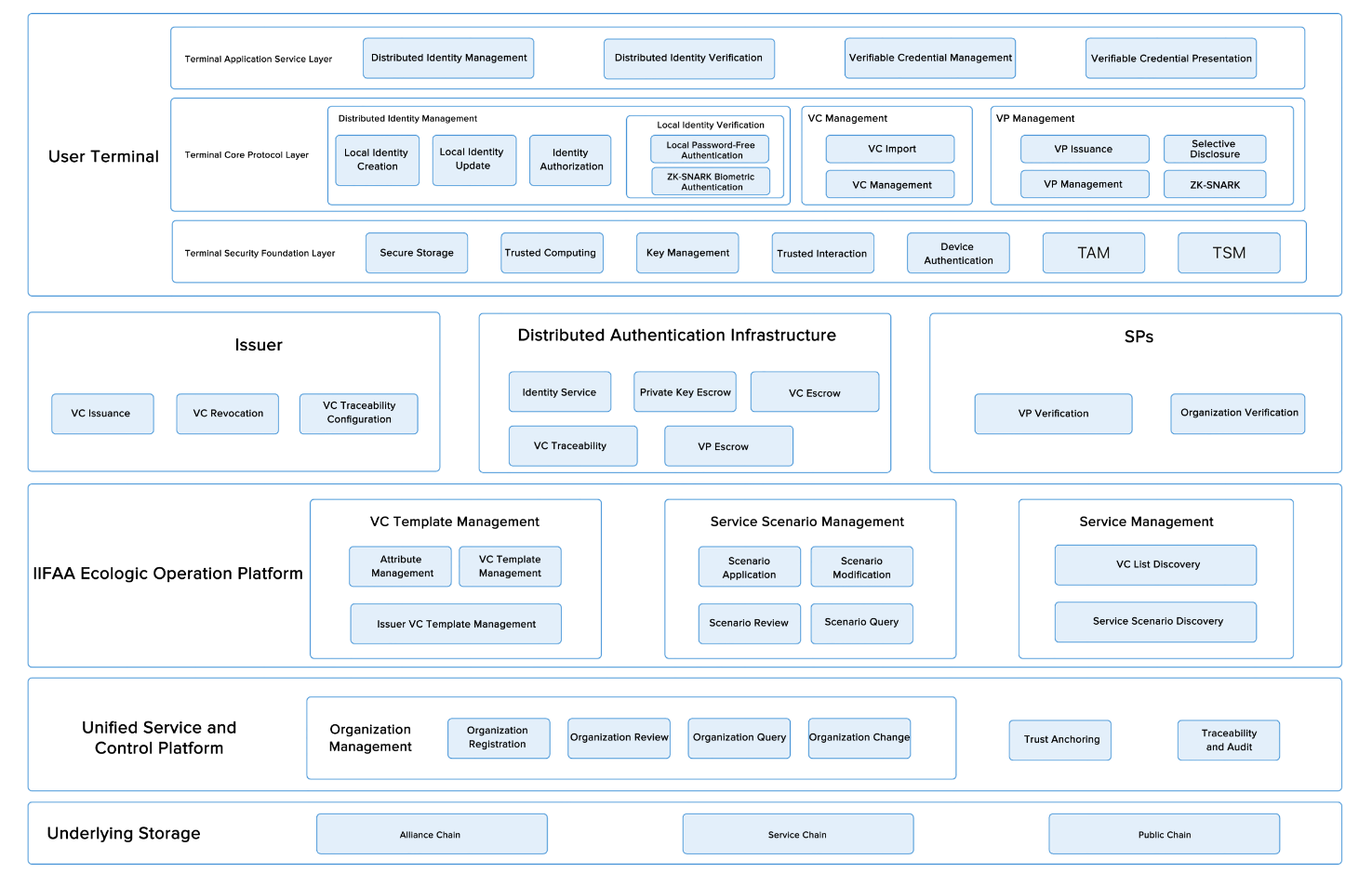
Figure 2 Technical Architecture
Comprising a terminal security foundation layer, core protocol layer, and application service layer, the decentralized
trusted authentication system provides services such as decentralized identity and VC information management for users.
These components collaborate to secure and maintain the confidentiality of user identities and VCs.
This layer provides security based on the terminal environment. Utilizing the terminal's Trusted Execution Environment
(TEE or SE) and SIM card security areas, it offers core security functionalities for higher-level services, including
but not limited to secure storage, trusted computing, key management, trusted interactions, and device authentication.
Building upon the security capabilities of the terminal security foundation layer, this layer offers unified
decentralized identity management services, including local identity creation and update, authorization, and
verification. Additionally, it provides VC management services, such as VC import and revocation, and verifiable
presentation management, including issuance, selective disclosure, ZK-SNARK, etc. These services enhance the security
and trustworthiness of decentralized identities, underpinning digital identity applications with robust terminal
foundation support.
Built on the DID core protocol layer, this layer links decentralized identity infrastructure, issuers, and service
providers to offer users complete decentralized trusted authentication capabilities and services.
Decentralized identity management involves storing and using decentralized identities on various user devices, including
but not limited to smartphones and servers. The requirements for decentralized identity management are as follows:
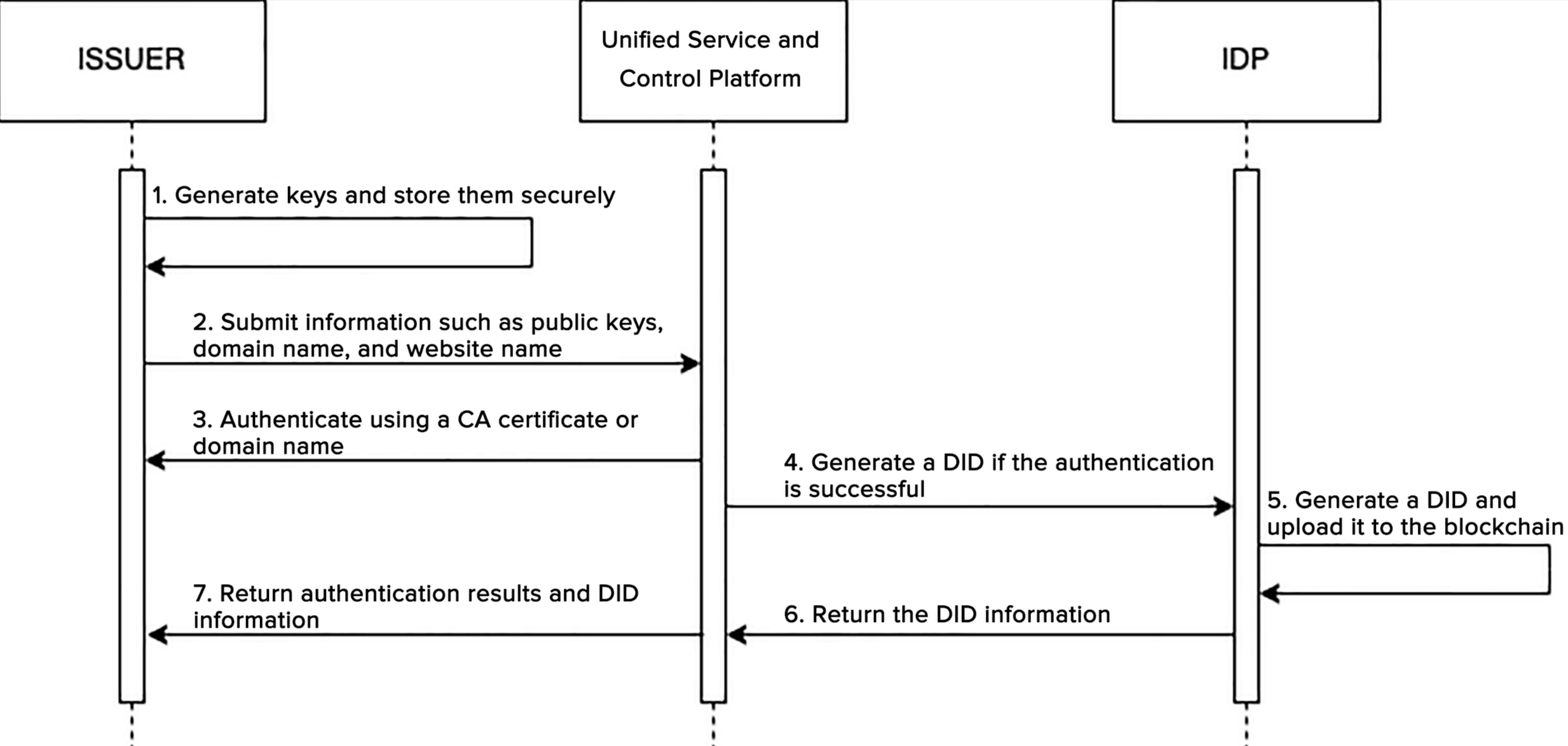
- Capability for decentralized identity registration, involving the generation of identity keys at the user's end during
registration, coupled with the generation of a complete decentralized identity document through the identity provider,
followed by blockchain storage;
- Capability for storage and utilization of decentralized identity keys, securely housed on the user side, to enable
operations such as data signing post user authorization;
- Capability for decentralized identity cancellation to allow users to actively deregister their decentralized identity
and change the status of the blockchain decentralized identity document to "Closed;"
- Provision of cryptographic security mechanisms to protect users' identity information from unauthorized access and cyber
attacks;
- Recommended ease of use and configuration to offer a user-friendly interface and experience for the registration and
management of decentralized identities.
Decentralized identity verification refers to the independent verification of identity by any organization within the
decentralized trusted authentication system, devoid of reliance on centralized nodes. By leveraging the terminal's
trusted environment, it combines verification methods like passwords and facial or fingerprint recognition with
technologies such as DPKI and ZK-SNARK. Verification key elements and methods are made public on the blockchain,
enabling any organization requiring user DID verification to independently access blockchain identity information and
complete identity verification through methods like private key signature validation and ZK-SNARK checks. The
requirements for decentralized verification are as follows:
- Identity verification capabilities use methods like passwords, fingerprints, or facial recognition to verify the current
user's identity and prevent identity impersonation, adhering to the fingerprint verification requirements specified in
IIFAA Local Password-Free Technology Specification 2.0;
- Operations based on trusted environments such as TEE or SE to ensure the trustworthiness of the identity verification
computational process;
- Blockchain publication of non-sensitive verification key elements and methods for autonomous identity verification by
any organization needing to verify user DID;
- Recommended ease of use and configuration to offer a user-friendly interface and experience for the utilization of
decentralized identity verification features.
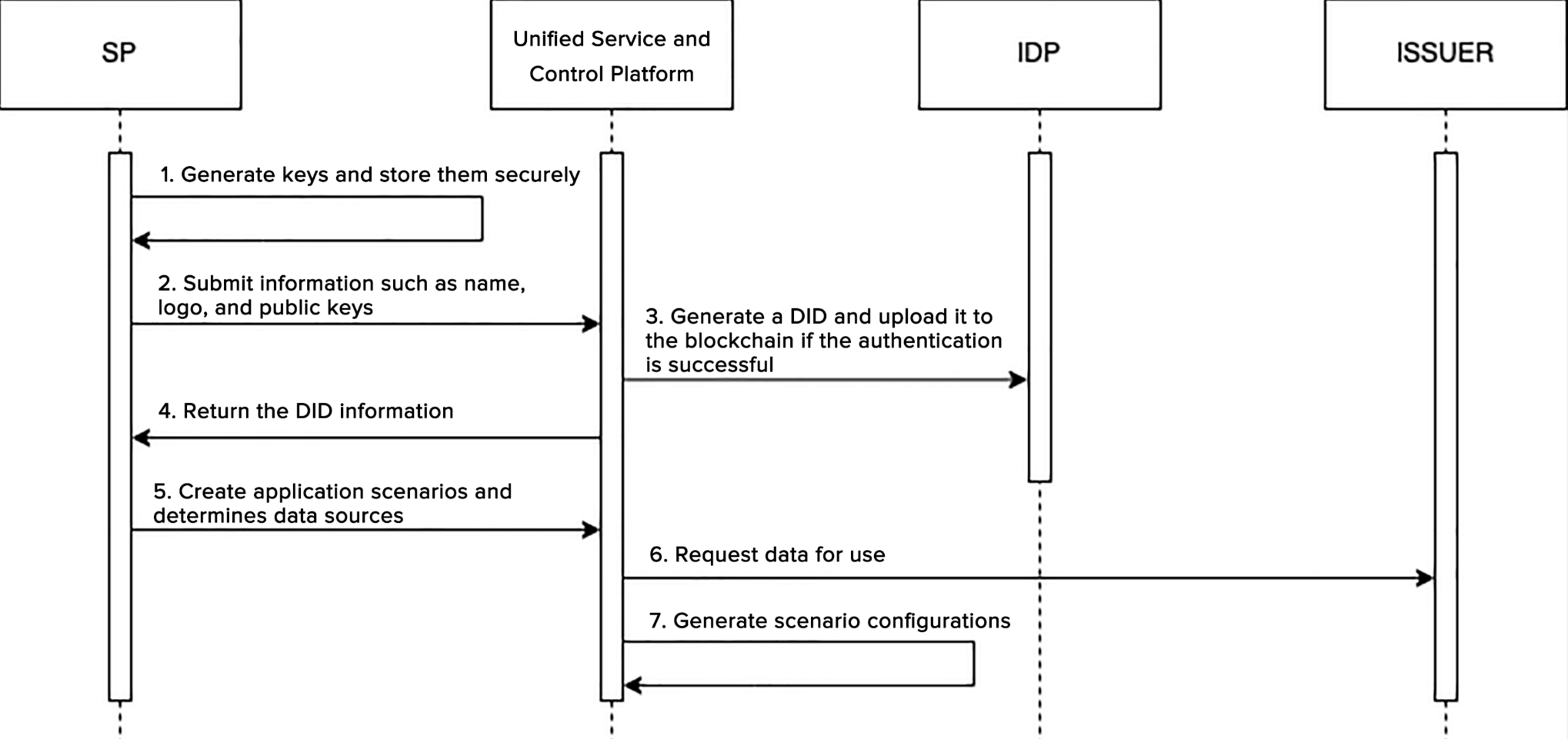
VC management involves centralized storage and management of various VCs, including legal identity credentials, service
credentials, and digital asset credentials. This ensures the security and validity of these VCs, preventing illegal use
and alteration. The requirements for VC management are as follows:
- VC import capability to allow the importation of VC data encrypted with the user's public key to the user side, followed
by decryption and persistent storage;
- Capability for VC summary sets query to access all VC summaries under a specified DID, including information like the
VC's issuers, types, etc.;
- Capability for detailed VC information query, including complete information of a specific VC ID;
- Capability to delete VCs to remove VC data corresponding to a specified VC ID.
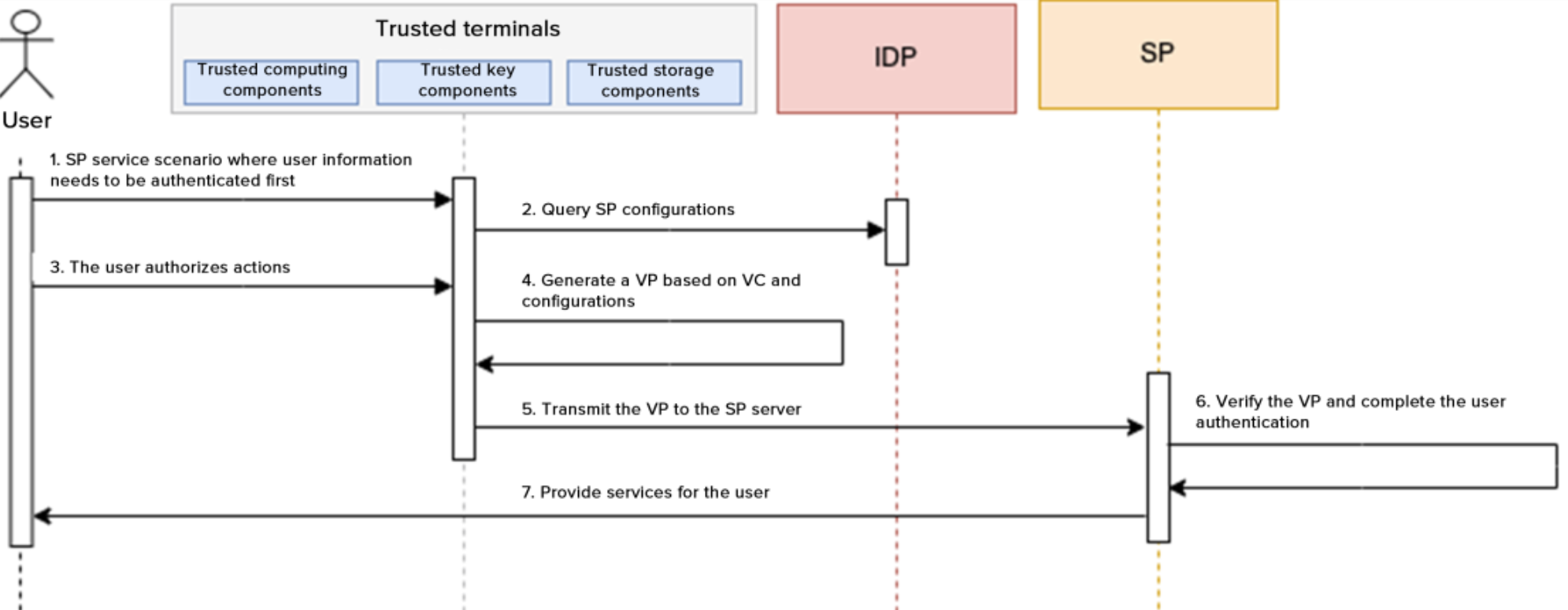
Based on current scenario requirements, users are provided with a selection and authorization of VC content that meets
the criteria. Following the principle of minimal privacy disclosure, users select and authorize the presentation of
relevant fields. Then, according to standard protocols, a VP is assembled, and signed with the DID private key, and the
signed VP information is presented to the scenario-based service provider for validation. Throughout the entire process,
the handling and signing of VCs are carried out within a secure environment on the user side. This is done following the
principle of minimal privacy disclosure for both selection and authorization, ensuring the security and privacy of user
data. The requirements for VC presentation functionality are as follows:
-
Adherence to the principle of minimal privacy disclosure when presenting relevant fields to safeguard user identity
information from leakage or misuse;
-
Assembling VP according to standard protocols and signing with the DID private key to ensure the authenticity and
completeness of VCs;
-
Completing VC processing and signing within a trusted environment like TEE or SE to guarantee the security and privacy
of user data.
The identity service requirements are as follows:
- DID service to implement the DID parsing layer, which enables the interaction with the blockchain through a smart
contract, for DID creation, query, modification, and deletion;
- Recommended alias service with functions such as quick use and retrieval of DIDs, including defining the basic alias
rules, maintaining the one-to-one mapping relationships between an alias and a DID, and implementing alias creation,
query, modification, and deletion.
The decentralized DID private key escrow service shall be provisioned based on technologies including but not limited to
MPC Key Share, TEE, privacy computing, access control and permission management, and multi-factor authentication (MFA).
The VC encryption escrow service shall be provisioned.
The VC traceability requirements are as follows:
- VC traceability, that is, when a user presents a VP containing a VC that needs to be traceable, the VC shall be
encrypted using a security key of the IIFAA decentralized infrastructure, and an interface shall be configured for SPs
to obtain the security key for decryption before authenticating the VP. VC traceability information is classified into
basic information and custom information. The basic information is stored in plaintext and contains issuer DID, SP DID,
VC type, VC presentation time, and VC authentication time. The custom information is encrypted for storage and includes
user DID, VC ID, and service scenarios.
- Capability to query VC traceability information, and provisioning of an interface for issuers to query the above VC
traceability information.
The VP encryption escrow capability shall be provisioned. That is, when a user encrypts a VP and submits the encrypted
VP to the platform, the platform returns a unique encrypted ID, based on which, SPs can query the encrypted VP.